
|
|
DYNAMIC SSH TUNNEL EXAMPLES• Dynamic SSH Tunnel (~VPN) • Curl With SOCKS SSH Tunnel • SSH Using An Existing SSH Tunnel • SSH Tunnel MQTT Data Example Dynamic SSH Tunnel (~VPN)
Curl With SOCKS SSH TunnelIf you want to grab a webpage's HTML code via curl then type the following:curl --proxy socks5h://localhost:5555 -k -u username:password https://127.0.0.1/your/path/to/the/webpage.php • The -k option prevents the verification of the SSL certificate (you may not want to do this unless you are using a self certified SSL certificate!). • The optional -u username:password is for an Apache Server Authentication prompt. Just remove this if you don't need it! SSH Using An Existing SSH Tunnel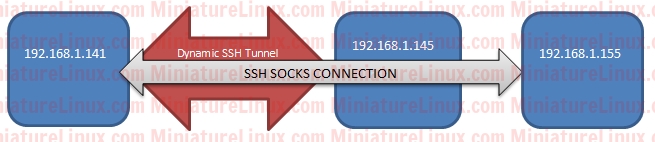 I'm demonstrating this by using three Linux Machines here: (1) Linux Box 1 192.168.1.145 (2) Linux Box 2 192.168.1.141 (3) Linux Box 3 1192.168.1.155 [on port 8080] Terminal A - Linux Box 2 (192.168.1.141): sudo ssh -D *:5555 root@192.168.1.145 –Nn Terminal B - Linux Box 2 (192.168.1.141): ssh -o ProxyCommand='nc -X 5 -x 127.0.0.1:5555 %h %p' 192.168.1.155 -p8080 Running the above ssh -o ProxyCommand='nc -X 5 -x 127.0.0.1:5555 %h %p' 192.168.1.155 -p8080 means you SSH into the Linux Box 3 (on port 8080). Now if you open another Terminal (C) on the Linux Box 2 (192.168.1.141): sudo tcpdump -i any port 5555 -n –A This Terminal (C) is now used for watching traffic move through port 5555... On the Terminal (B) which has already SSHed into the Linux Box 3, start typing or press the return key whist watching Terminal (C). You will observe that data is being fired out as you press a key in the terminal. So the the data is going through port 5555 on 192.168.1.141 (The Linux Box 2). If you now for example reboot the Linux Box 1 (192.168.1.145), the Terminal (B) which is SSHed into the Linux Box 3 via my SSH SOCKS Tunnel will drop (i.e. because you decided to sever the connection via rebooting). That is to say, the Tunnel breaks as you would fully expect... SSH Tunnel MQTT Data ExampleA remote machine with IP Address 187.43.152.345 is running a Mosquitto Broker on port 1883 (187.43.152.345:1883). You have already setup RSA Keys on the Mosquitto broker machine and your local machine (laptop).I wish to be able to see this MQTT data on my laptop via my laptops mosquitto broker while sitting in an internet cafe somewhere in the world... therefore I can setup an SSH Tunnel so that port 2883 on my local machine (my laptop in the internet cafe) receives said MQTT data from the remote machine (187.43.152.345) which uses the default 1883 port for MQTT. sudo ssh -L 2883:127.0.0.1:1883 187.43.152.345 –N Note that you can fork this into the background via using -f if you want (or add & to the end of the command). -L => Local tunnel 2883 => Local port number on the laptop 127.0.0.1 => The remote computers localhost ip address (i.e. perspective of the tunnel end point) 1883 => Mosquitto Broker's MQTT port on the remote machine -N => Fore SSH not to run a command on the remote machine On a terminal on the laptop type: (1) mosquitto_sub -h 127.0.0.1 -v -p 2883 -u MosquittoUsername -P MosquittoPassword -t '#' In another terminal, SSH into the remote MQTT Machine (using RSA keys here): sudo ssh 187.43.152.345 Get some live streaming MQTT data from the Mosquitto broker: (2) mosquitto_sub -t '#' -v -u MosquittoUsername -P MosquittoPassword Comparing the terminal outputs of (1) and (2) above, you will note that the local laptop Mosquitto broker using port 2883 (1) is identical to the remote machine Mosquitto output using port 1883 (2). In otherwords the MQTT data is being successfully tunneled over SSH. And of course you can send MQTT data from your laptop via the SSH Tunnel to the remote MQTT Mosquitto Broker at 187.43.152.345: mosquitto_pub -h 127.0.0.1 -p 2883 -t Tester -m "**** MESSAGE SENT FROM MY LAPTOP Via AN SSH TUNNEL ****" -u MosquittoUsername -P MosquittoPassword |
|
Linux Examples - Comments |
||